In the not-too-distant future, you just might see household appliances turn into botnets attempting to sign up for accounts on your website — instead of a wolf in sheep’s clothing, you’d have botnets of devices trying to pass themselves off as human beings. Security worries appear to go hand-in-hand with the Internet of Things.
As IoT moves beyond wearables and into household appliances, industrial machinery and automobiles all connected to the Internet — so expand the possibilities for Terminator-like scenarios where gizmos become part of botnets that attempt to hack into your business.
Already, fixing problems introduced by IoT are expected to account for 20% of security budgets by 2020, according to Gartner Group.
Gartner says this security headache will be fueled by the growth of a black market that could exceed $5 billion in sales of fake sensor and video data by 2020. This will enable all kinds of criminal activity and privacy breaches.
What to Do About the Internet of Things
A defense against all of these horrors begins with keeping out those with malicious intentions. Put two-factor authentication at an organization’s perimeter — including it in onboarding — to block the threat actors from entering the target’s business in the first place.
Now’s a good time to start blocking suspicious sign-ups from coming into your business’ website or network — IoT is already gaining ground.
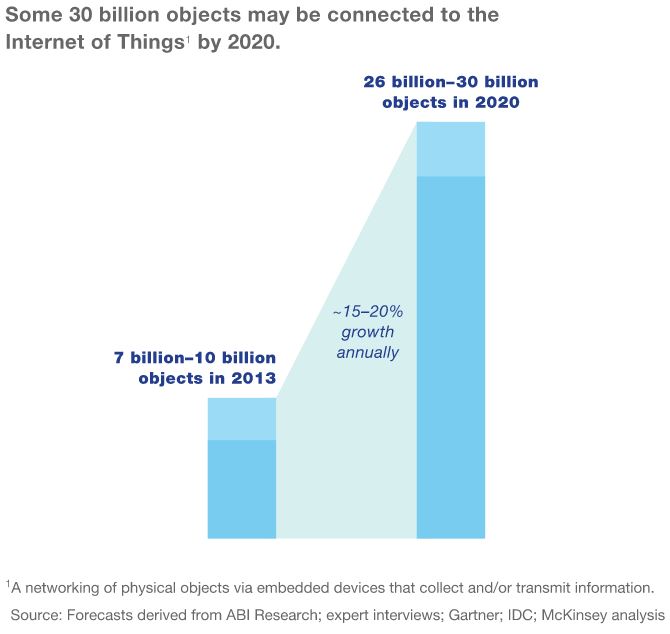
Gartner Group estimates that more than half of major new business systems and processes will have an IoT component by 2020. And Gartner says there will be almost 20 billion of the devices in circulation by 2020, generating more than $300 billion in apps and service-related revenues.
Total spending on endpoints and services for IoT may reach nearly $2 trillion by the end of 2017, with 8.4 billion of these gizmos connected to the Internet worldwide, according to Gartner.
While expectations for IoT device growth vary to some degree based on the source, there appears to be some consensus about security concerns.
It’s actually making consumers hesitant to buy IoT devices — about 71% of Americans are worried that smart home appliances might steal their personal data, according to a survey by iControl Networks.
Businesses are worried as well: While 85% of those surveyed by AT&T have at least the intention of deploying IoT devices, only 10% feel confident that they could protect the gizmos against hackers.
Solutions being suggested for the IoT landscape entail protection for more than the actual hardware itself, but rather building security into all of the software applications and network connections that IoT can access.
This begins with adding security to the onboarding process from the get-go so that perpetrators with ill intentions don’t get in and wreak havoc.
All Preventable
A recent study of IoT vulnerabilities reported between November 2015 and September 2016 found that 100% of them were completely avoidable — all preventable if the device manufacturers and developers had implemented security and privacy principles outlined in the Online Trust Alliance’s IoT Trust Framework.
The organization’s framework notes the following eight items as the most glaring points of vulnerability:
- Insecure credential anagement including making administrative controls open and discoverable
- Not adequately and accurately disclosing consumer data collection and sharing policies and practices
- The omission or lack of rigorous security testing throughout the development process including but not limited to penetration testing and threat modeling
- The lack of a discoverable process or capability to responsibly report observed vulnerabilities
- Insecure or no network pairing control options (device to device or device to networks)
- Not testing for common code injection exploits
- The lack of transport security and encrypted storage including unencrypted data transmission of personal and sensitive information including but not limited to user ID and passwords
- Lacking a sustainable and supportable plan to address vulnerabilities through the product lifecycle
While many security products are so complex that sustaining and supporting them can easily exceed a company’s means, user authentication via SMS remains very doable. Learn more about how this might work for your company by clicking here.

 Security
Security