For most businesses that are building a trustworthy user community, empowering sharing economy, selling online goods, or making online reservations for services, ensuring that the user is real, and contactable, is of paramount importance, to fight fraud, and craft wonderful customer experiences. The most effective way to do that is to use 2FA (two-factor authentication) SMS; a single-use PIN code is sent via SMS to a phone number, and the user proves that he owns the phone number by clicking on the link in the SMS. 2FA SMS is a unique 2FA as it not only verifies that the person is legitimate but also that the person can be contactable through that phone number.
Once you have implemented 2FA SMS to fight fraud, you are now exposed to a different type of threat; bots can request for 2FA SMS for any phone numbers, thus racking up your SMS expenditure – resource (your expenditure) exhaustion attack.
Thus although there are a lot of SMS providers with which you can build your 2FA SMS solution, RingCaptcha stands out because of 2 significant advantages: implementation simplicity, and in-built resource exhaustion attack protection.
RingCaptcha has a widget (below) that you can easily implement by pasting a small code snippet on your web page. The widget helps you collect user information, and also verifies the user’s phone number by sending a 2FA SMS. Upon verification, it can perform a customized action of your choice, e.g., register the user in your database.
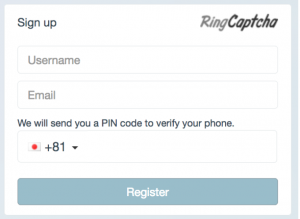
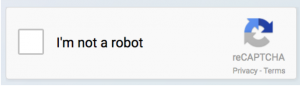
The new version 2 beta of our widget now incorporates Google’s reCaptcha technology, which can differentiate a human from a bot using a simple user interface shown below:
reCaptcha relies on a slew of heuristics (e.g., the movement of the mouse cursor, etc.) to determine whether a bot or a human clicked on the “I’m not a robot” checkbox. Only upon passing the “I’m not a robot” test, will the user be shown the RingCaptcha widget, which can then be used to verify the user’s phone number using a 2FA SMS.
You are not alone, if you are thinking that Internet attacks will not happen to you. To coax you out of that mindset, we encourage you to hop over to ThreatMap, and enjoy the beautiful pattern of chaos overlayed on the world map, created by lines delineating the combination of source, destination, and attack types. The number of attacks ongoing each minute will just convince you otherwise.
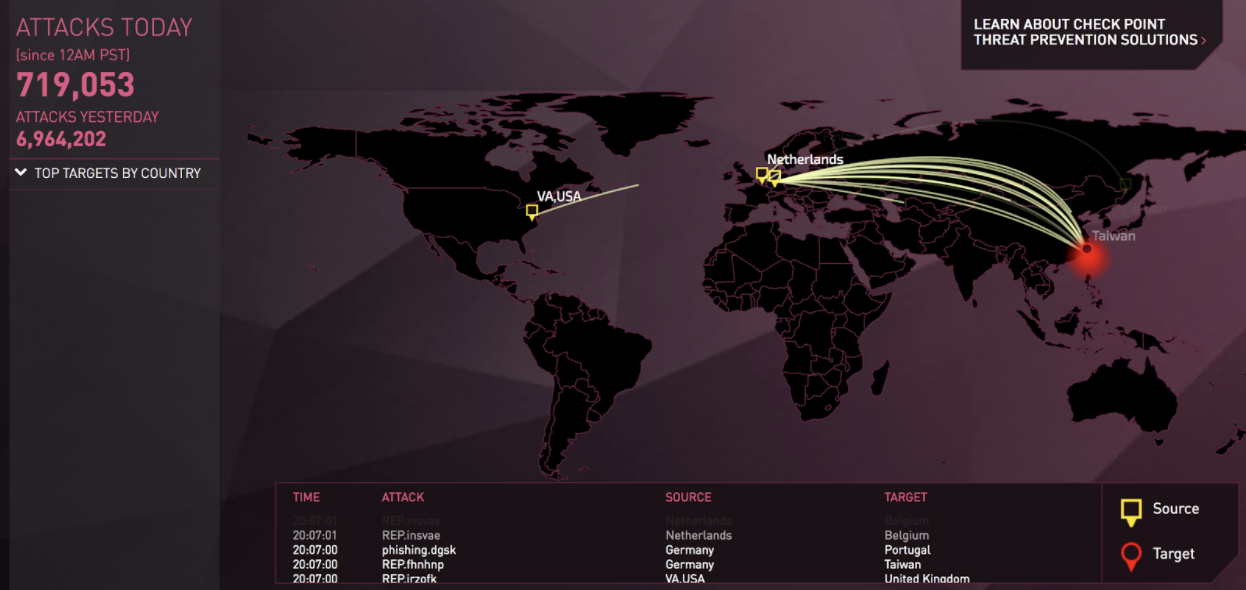
Courtesy: https://threatmap.checkpoint.com/ThreatPortal/livemap.html
Interested to use version 2 beta of the widget? Please contact us through live chat at the bottom right of our new website!

 Security
Security