Two-Factor Authentication
Furthermore, it's also a bit misleading to call token-based authentication stronger than two-factor authentication, given that you can consider users' mobile phones to be the hardware level of authentication. And if a technology introduces friction into a process that sends your intended users scurrying, how is that security making you any more secure -- and where is the ROI in something no one's using?
The average company spends $4 million in the aftermath of a data breach, according to the Ponemon Institute.
It's Complicated
If you add hardware tokens to the process, it ends up being overkill unless you're authenticating enterprise users at a company with higher risk like a financial institution or government agency. And even then, adding additional hardware to the process complicates things. First there's the added expense of the key fobs or card readers, including replacements if they are lost or broken. Then there's the time delay involved in granting these devices to the intended recipients. Okay, enterprise users can wait (or their managers can plan ahead for issuance to new hires) but not customers who are onboarding -- they're almost guaranteed to click elsewhere instead of waiting. Even for enterprise users, tokens can be a hassle because they need to be managed by a specially skilled administrator. However if you designate the token to be users’ smartphones or tablets, that can make things much more cost effective – both in savings on hardware as well as staffing.Simple Can Be Priceless
Not requiring extra staff help is priceless in today's economy -- especially for companies that are small or still in the start-up stage. The shortage of security experts far exceeds what most people realize. Demand for cybersecurity professionals outstrips supply so greatly that a third of companies go without the talent they need for at least six months -- if a candidate with the desired qualifications ever shows up at all. Such is the tech talent shortage quantified by ISACA in its third annual survey, State of Cyber Security 2017: Current Trends in Workforce Development. The majority of the 633 security professionals ISACA surveyed said they fear they are underprepared for threats -- the two charts below illustrate why.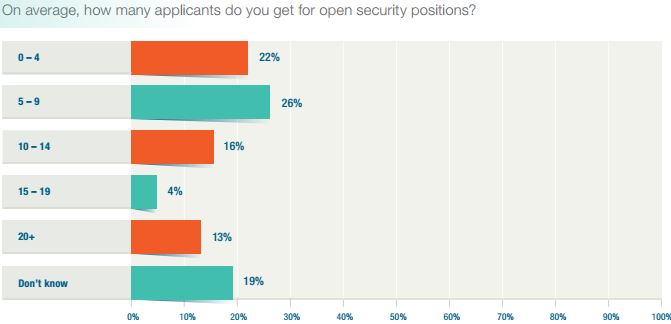
There just aren't enough qualified cybersecurity experts to go around, or so it seems. This skills gap is illustrated in ISACA's latest annual survey of workforce trends.
A Small Fraction
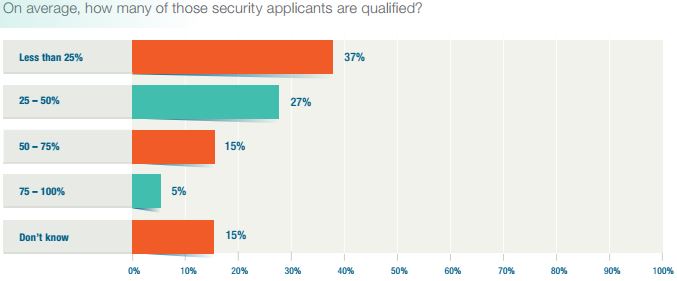
Applications to information security job openings yield a small fraction of what the average job posting fetches across industries. Most corporate job openings result in 60 to 250 applicants, but a cybersecurity job opening -- well, 59% of those surveyed by ISACA said they receive at least five applications per posting and only 13% said they receive 20 or more per listing. Most of these applicants are unqualified: 47% of respondents said that less than one in four candidates actually have the qualifications needed to keep their companies secure. However, foregoing security because you can't find the right people to administer it is dangerous. And that's an understatement.Skyrocketing Cybercrime
Estimates of losses from cybercrime continue to skyrocket. The most aggressive of these statistics we've seen so far puts the total annual cost at $6 trillion in 2021. Okay, we'll let you catch your breath. This figure from Cybersecurity Ventures includes intellectual property theft, damage and destruction of data, disruption of business, forensic investigation and repairing reputational harm. It's unclear whether that also includes spending on technology and services for fighting off attacks, which CyberSecurity Ventures pegs at $175 billion by 2020.Cleanup Jobs
An overlooked subset of that cybercrime tab includes cleaning up the damage from attacks introduced by fake users. Companies spend an average of at least $4 million apiece to address fraud or spam perpetrated by fake users, said a survey by the Ponemon Institute. The majority of these expenditures go toward reputation repair after the fact. In spite of this, a stunning 58% of companies surveyed by Ponemon did not have a formal process for determining the legitimacy of users.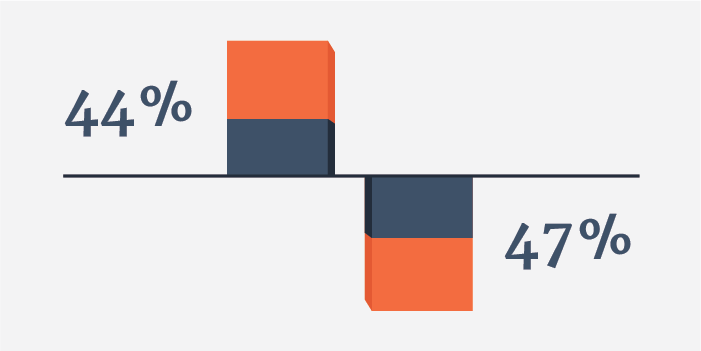
Grow the value of your user base 44% by weeding out fake users -- but not doing so means a loss of 47%, according to The Ponemon Institute


 Verification
Verification 

